
In short, Null session attack is an exploit that uses unauthenticated NetBIOS connections to enumerate a target host.Previously, you learnt about Ethical Hacking, Spoofing, Phishing, Hacking, Password crackers etc. Keeping this informative and educative series on, today i would like to describe to you about Null Session Attacks and how they can let your computer be compromised in no time. I will also write about the ways by which you can protect your computers/servers against the same.
Windows machines allows remote users to login remotely to a machine running the server service. This login can then be used to use a shared resource, such as a printer or any other shared directory etc. Once the user is logged in their connection to the remote machine is referred to as a “session”. The number of open sessions in a windows machine can be checked using multiple ways, one of the most widely used way is by exploring the open sesions using ” Computer Management” as shown in the figure below.
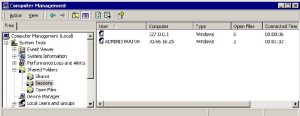
Open Sessions on your computer
Usually Microsoft Windows Servers run many services and programs. Some of these services then communicate with other windows servers to complete some specific tasks. For such communications and tasks to complete successfully, windows servers also logs into a remote windows server using a blank username and password. This is referred as a “Null Session”.
However, its not only always the genuine servers that can login to the remote server but also hackers who have enough skills can do so and its not that tough either. They can use this to obtain NetBios information from this machine, and to perform various other exploits against this machine. This is referred to as a “Null Session Attack”.
To carry out a Null Session attack , all that a hacker needs is cmd.exe ( command prompt ) and PSTools ( Available from Sysinternals). If you have the IP Address of your target follow the steps below to create a Null Session Login to the remote machine. 1.) At Run , Type cmd
2.) At the command prompt, enter the following
net use \\IP ADDRESS\ipc$ /user:administrator
For eg. If the target address is 72.233.2.54 type in net use \\72.233.2.54\ipc$ /user:administrator
3.) If you receive the message ” The command was successfully executed”, it means that you have logged in using a Null Session.
4.) Now, if you wish, you can get loads of information about this system.Information that can be obtained includes user IDs, share names, security policy settings, users currently logged in and more. The Windows registry can even be tapped remotely with the right tools.
5.) Lets try getting hold of the valid usernames for this remote system. For this, you would need a tool called PsTools from Sysinternals. Download it from here. 6.) Once you have downloaded the zip file, extract and copy the files “psexec” and “psloggedon” to the ‘C:\Windows\System32′ folder.
7.) Enter at the command prompt the command
psexec \\IP ADDRESS -u administrator psloggedon \\IP ADDRESS
If the computer you have identified as a target is not sufficiently protected, you should get all the users logged on to this computer.
How to protect your computer from a Null Session Attack?
Null Session Attacks are mostly carried out on ports 139 and 445 on aWindows PC. Therefore the best option is to is to simply block SMB communications by limiting traffic on TCP ports 139 and 445 (excluding NT which doesn’t use 445) to trusted networks. I know it seems painfully obvious, but people still have unprotected Windows systems out there for the taking. A basic firewall and host-based IPS can do wonders for this.
If you use Windows XP, install service pack 3 without any delays. SP3 has an improved firewall which prevents null session attacks, so that at least if someone tries to login to your computer over the internet, it is blocked.






not working for me
ReplyDelete